June 30, 2023
Published by webence on June 30, 2023
Categories
Cloud account takeover has become a major problem for organizations. Think about how much work your company does that requires a username and password. Employees end […]
June 30, 2023
Published by webence on June 30, 2023
Categories
In recent years, electronic mail (email for short) has become an essential part of our daily lives. Many people use it for various purposes, including business […]
June 6, 2023
Published by webence on June 6, 2023
Categories
In today’s digital age, technology plays a significant role in our lives. But along with the rapid advancements and innovations, several myths have persisted. Is it […]
January 13, 2023
Published by webence on January 13, 2023
Categories
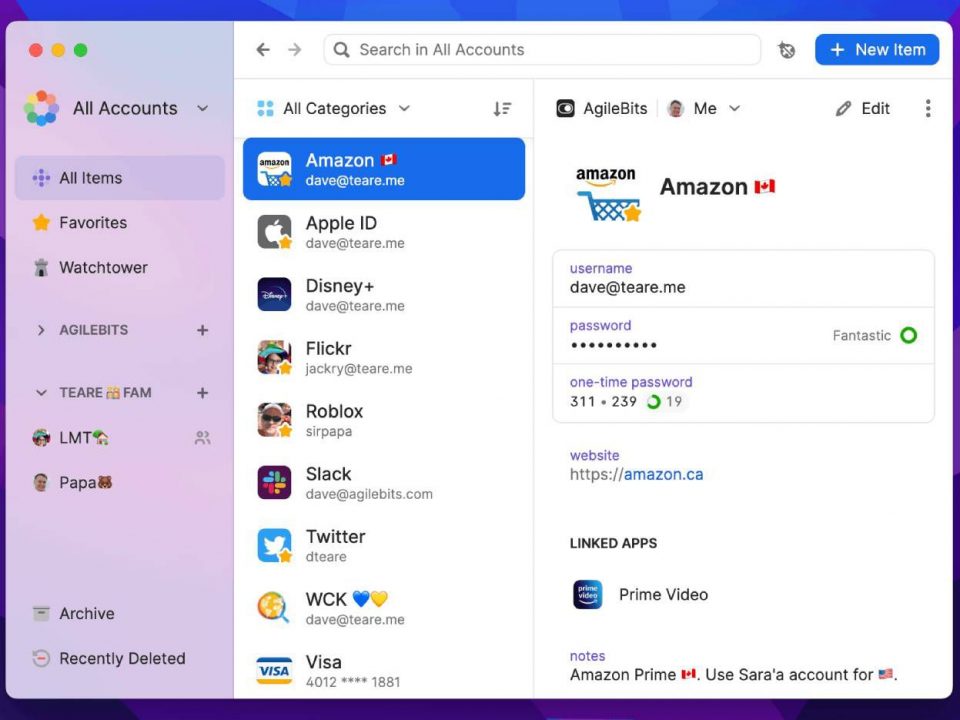
A password manager is a tool that helps you generate and store unique, complex passwords for each of your online accounts. These tools can be a […]
January 12, 2023
Published by webence on January 12, 2023
Categories
Endpoint protection, also known as endpoint security, is a critical aspect of keeping your Mac safe from malware and other cyber threats. In this blog post, […]
December 12, 2022
Published by webence on December 12, 2022
Categories
It goes without saying that your data is vitally important to your business. Lose data, and you could be out of business for a while, or […]
December 12, 2022
Published by webence on December 12, 2022
Categories
Part of the problem with a data breach is that your business doesn’t know about it until it’s already happened – sometimes well after. Knowing the […]
December 12, 2022
Published by webence on December 12, 2022
Categories
Many of us look forward to January 1 as a fresh start. But before we get to hit that refresh button, it’s a good idea to […]
December 12, 2022
Published by webence on December 12, 2022
Categories
A new year is a chance for a fresh beginning. To that end, try these tech tips for small business owners to kick 2023 off right. […]